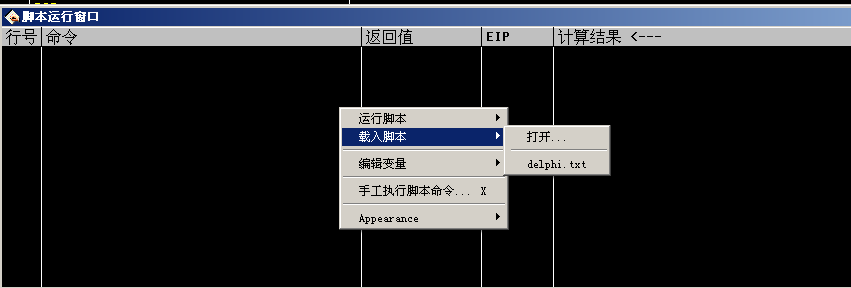
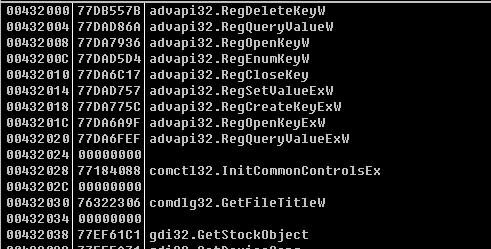
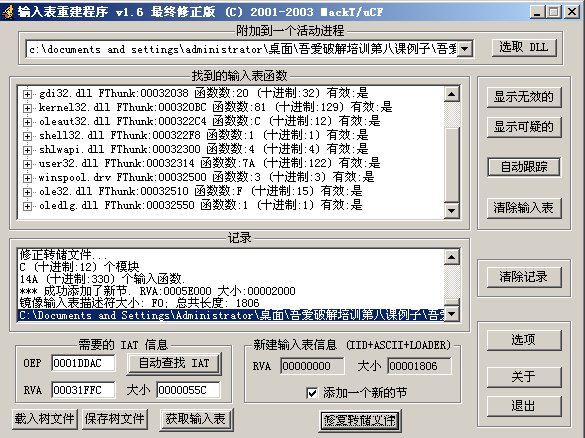
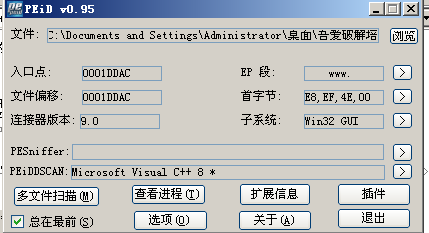
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
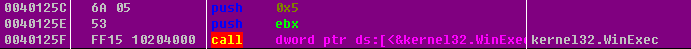
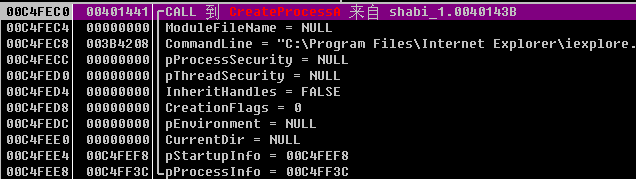
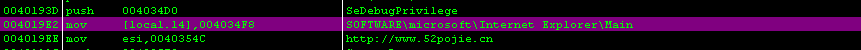
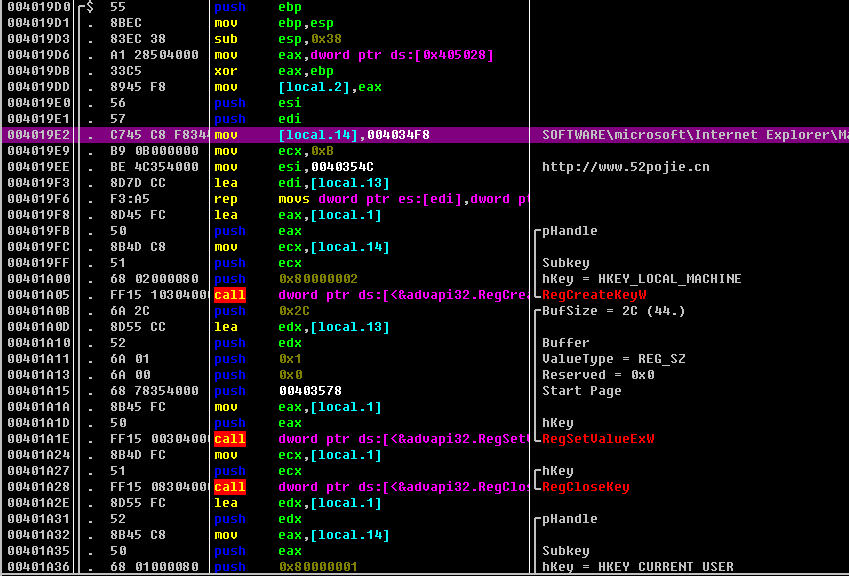
| 00402A60 /. 55 push ebp
00402A61 |. 8BEC mov ebp,esp
00402A63 |. 6A FF push -0x1
00402A65 |. 68 FB385300 push 005338FB
00402A6A |. 64:A1 00000000 mov eax,dword ptr fs:[0]
00402A70 |. 50 push eax
00402A71 |. 81EC 1C010000 sub esp,0x11C
00402A77 |. A1 B0275900 mov eax,dword ptr ds:[0x5927B0]
00402A7C |. 33C5 xor eax,ebp
00402A7E |. 8945 F0 mov [local.4],eax
00402A81 |. 53 push ebx
00402A82 |. 56 push esi
00402A83 |. 57 push edi
00402A84 |. 50 push eax
00402A85 |. 8D45 F4 lea eax,[local.3]
00402A88 |. 64:A3 00000000 mov dword ptr fs:[0],eax
00402A8E |. 8BF9 mov edi,ecx
00402A90 |. 89BD E4FEFFFF mov [local.71],edi
00402A96 |. E8 2E4B0000 call 004075C9
00402A9B |. FFB7 B8000000 push dword ptr ds:[edi+0xB8] ; /lParam
00402AA1 |. 8B35 44385400 mov esi,dword ptr ds:[<&USER32.SendMessageA>] ; |user32.SendMessageA
00402AA7 |. 6A 01 push 0x1 ; |wParam = 0x1
00402AA9 |. 68 80000000 push 0x80 ; |Message = WM_SETICON
00402AAE |. FF77 20 push dword ptr ds:[edi+0x20] ; |hWnd
00402AB1 |. FFD6 call esi ; \SendMessageA
00402AB3 |. FFB7 B8000000 push dword ptr ds:[edi+0xB8] ; /lParam
00402AB9 |. 6A 00 push 0x0 ; |wParam = 0x0
00402ABB |. 68 80000000 push 0x80 ; |Message = WM_SETICON
00402AC0 |. FF77 20 push dword ptr ds:[edi+0x20] ; |hWnd
00402AC3 |. FFD6 call esi ; \SendMessageA
00402AC5 |. 68 04010000 push 0x104
00402ACA |. 33DB xor ebx,ebx
00402ACC |. 8D85 ECFEFFFF lea eax,[local.69]
00402AD2 |. 53 push ebx
00402AD3 |. 50 push eax
00402AD4 |. E8 E7971100 call 0051C2C0
00402AD9 |. 83C4 0C add esp,0xC
00402ADC |. 8D85 ECFEFFFF lea eax,[local.69]
00402AE2 |. 50 push eax ; /Buffer
00402AE3 |. 68 04010000 push 0x104 ; |BufSize = 104 (260.)
00402AE8 |. FF15 14345400 call dword ptr ds:[<&KERNEL32.GetCurrentDirectoryA>] ; \GetCurrentDirectoryA
00402AEE |. 8D85 ECFEFFFF lea eax,[local.69]
00402AF4 |. 50 push eax
00402AF5 |. 8DB7 BC000000 lea esi,dword ptr ds:[edi+0xBC]
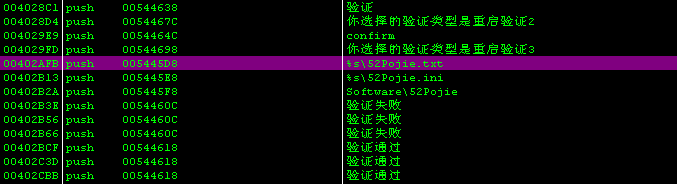
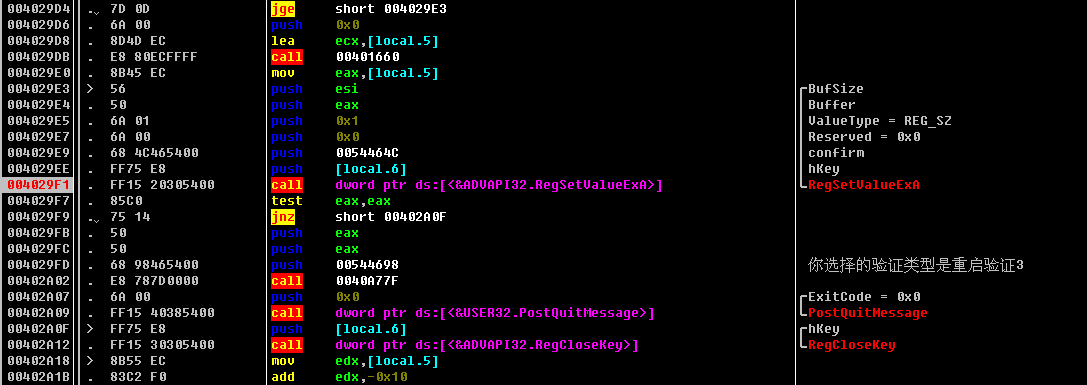
00402AFB |. 68 D8455400 push 005445D8 ; %s\52Pojie.txt
00402B00 |. 56 push esi
00402B01 |. E8 8AE9FFFF call 00401490 ; CString 拼接函数
00402B06 |. 8D8D ECFEFFFF lea ecx,[local.69]
00402B0C |. 51 push ecx
00402B0D |. 8D87 C0000000 lea eax,dword ptr ds:[edi+0xC0]
00402B13 |. 68 E8455400 push 005445E8 ; %s\52Pojie.ini
00402B18 |. 50 push eax
00402B19 |. 8985 E0FEFFFF mov [local.72],eax
00402B1F |. E8 6CE9FFFF call 00401490
00402B24 |. 8D87 C4000000 lea eax,dword ptr ds:[edi+0xC4]
00402B2A |. 68 F8455400 push 005445F8 ; Software\52Pojie
00402B2F |. 50 push eax
00402B30 |. E8 5BE9FFFF call 00401490
00402B35 |. 83C4 20 add esp,0x20
00402B38 |. 8D87 3C010000 lea eax,dword ptr ds:[edi+0x13C]
00402B3E |. 68 0C465400 push 0054460C ; 验证失败
00402B43 |. 8BC8 mov ecx,eax
00402B45 |. 8985 DCFEFFFF mov [local.73],eax
00402B4B |. E8 70990100 call 0041C4C0 ; 标签初始化
00402B50 |. 8D8F B0010000 lea ecx,dword ptr ds:[edi+0x1B0]
00402B56 |. 68 0C465400 push 0054460C ; 验证失败
00402B5B |. E8 60990100 call 0041C4C0
00402B60 |. 8D8F 24020000 lea ecx,dword ptr ds:[edi+0x224]
00402B66 |. 68 0C465400 push 0054460C ; 验证失败
00402B6B |. E8 50990100 call 0041C4C0
00402B70 |. 8B06 mov eax,dword ptr ds:[esi]
00402B72 |. 83E8 10 sub eax,0x10
00402B75 |. 50 push eax
00402B76 |. E8 F5F3FFFF call 00401F70
00402B7B |. 83C4 04 add esp,0x4
00402B7E |. 8D70 10 lea esi,dword ptr ds:[eax+0x10]
00402B81 |. 56 push esi ; /FileName
00402B82 |. FF15 0C345400 call dword ptr ds:[<&KERNEL32.GetFileAttributesA>] ; \GetFileAttributesA
00402B88 |. 33C9 xor ecx,ecx
00402B8A |. 83F8 FF cmp eax,-0x1 ; 判断文件是否存在
00402B8D |. 0F95C1 setne cl
00402B90 |. 83C6 F0 add esi,-0x10
00402B93 |. 83CF FF or edi,0xFFFFFFFF
00402B96 |. 8BC7 mov eax,edi
00402B98 |. 898D E8FEFFFF mov [local.70],ecx
00402B9E |. 8D4E 0C lea ecx,dword ptr ds:[esi+0xC]
00402BA1 |. F0:0FC101 lock xadd dword ptr ds:[ecx],eax
00402BA5 |. 48 dec eax
00402BA6 |. 85C0 test eax,eax
00402BA8 |. 7F 08 jg short 00402BB2
00402BAA |. 8B0E mov ecx,dword ptr ds:[esi]
00402BAC |. 56 push esi
00402BAD |. 8B01 mov eax,dword ptr ds:[ecx]
00402BAF |. FF50 04 call dword ptr ds:[eax+0x4]
00402BB2 |> 399D E8FEFFFF cmp [local.70],ebx
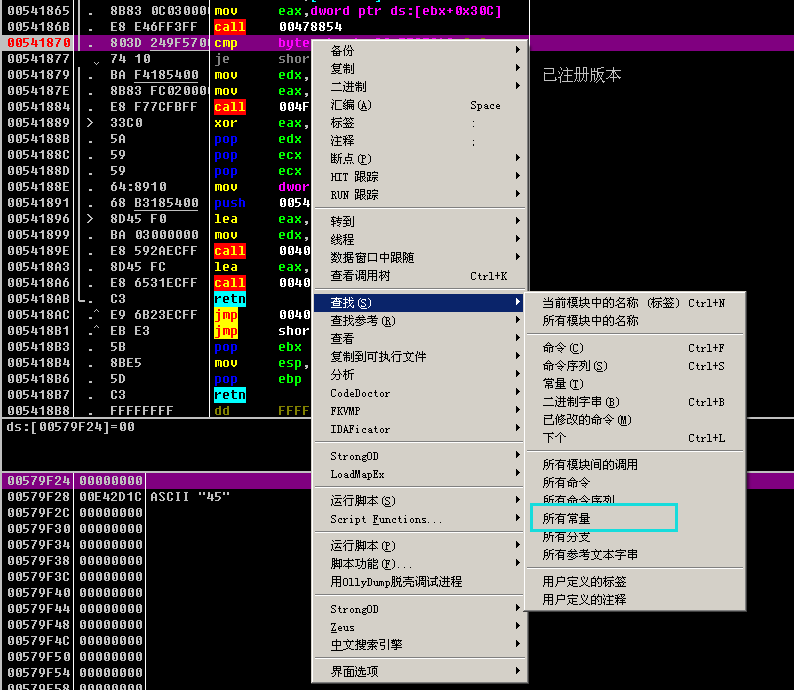
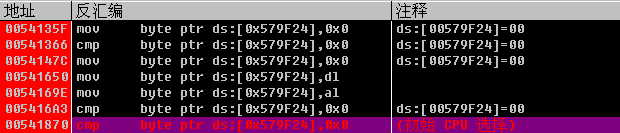
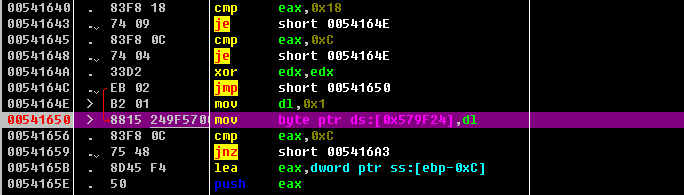
00402BB8 |. 74 24 je short 00402BDE ; nop 掉,或者跟入算法call
00402BBA |. 8B8D E4FEFFFF mov ecx,[local.71]
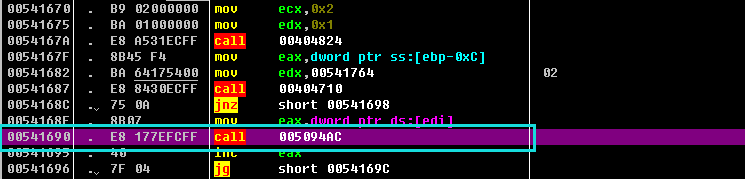
00402BC0 |. E8 1BF4FFFF call 00401FE0 ; 算法call
00402BC5 |. 85C0 test eax,eax
00402BC7 |. 74 15 je short 00402BDE
00402BC9 |. 8B8D DCFEFFFF mov ecx,[local.73]
00402BCF |. 68 18465400 push 00544618 ; 验证通过
00402BD4 |. E8 E7980100 call 0041C4C0
00402BD9 |. BB 01000000 mov ebx,0x1
00402BDE |> 8B85 E0FEFFFF mov eax,[local.72]
00402BE4 |. 8B00 mov eax,dword ptr ds:[eax]
00402BE6 |. 83E8 10 sub eax,0x10
00402BE9 |. 50 push eax
00402BEA |. E8 81F3FFFF call 00401F70
00402BEF |. 83C4 04 add esp,0x4
00402BF2 |. 8D70 10 lea esi,dword ptr ds:[eax+0x10]
00402BF5 |. 56 push esi ; /FileName
00402BF6 |. FF15 0C345400 call dword ptr ds:[<&KERNEL32.GetFileAttributesA>] ; \GetFileAttributesA
|